We use cookies to make your experience better. By continuing to visit this website you agree to our use of cookies. More information can be found in our Privacy Policy.
SSH
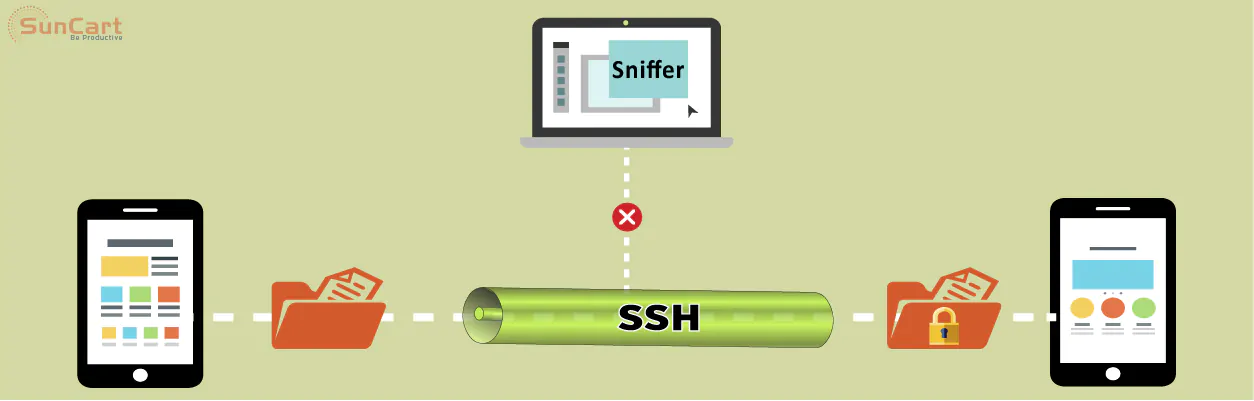
SSH (Secure Shell) - It is a network protocol used for performing an operation on network services securely over a less secure network like the internet. It provides a channel which is secured for remote login to any system.
Any service on the network can be made secure by SSH. It provides a better option for authentication by implementing strong encryption of data. Over a client-server architecture, the SSH provides a secure channel from the client application to the server computer.
It was designed as an alternative to the traditional protocols like TELNET which were used to remotely access computers. Protocols like TELNET were not secured, the passwords sent on the network appeared to be in plain text and the data were not encrypted. This made the network vulnerable because hackers could easily intercept and access the data.
The data sent using the SSH protocol are highly encrypted making them more secure by ensuring the confidentiality and integrity of data over an unsecured network like the internet.
How Does SSH Work?
If you’re using Linux or Mac, then using SSH is very simple. If you use Windows, you will need to utilize an SSH client to open SSH connections. The most popular SSH client is Putty.
For Mac and Linux users, head over to your terminal program and then follow the procedure below:
The SSH command consists of 3 distinct parts:
ssh {user}@{host}
ssh
The SSH key command instructs your system that you want to open an encrypted Secure Shell Connection.
{user}
This represents the account you want to access. For example, you may want to access the root user, which is basically synonymous for a system administrator with complete rights to modify anything on the system.
{host}
It refers to the computer you want to access. This can be an IP Address (e.g. 244.235.23.19) or a domain name (e.g. www.xyzdomain.com).
When you hit enter, you will be prompted to enter the password for the requested account. When you type it in, nothing will appear on the screen, but your password is, in fact being transmitted. Once you’re done typing, hit enter once again. If your password is correct, you will be greeted with a remote terminal window.
Uses of SSH
On client-server architecture there are several uses of SSH under many different contexts, following are some of the uses of SSH:
- SSH provides secure access to remote systems.
- It provides passing of commands on the remote host.
- Through SSH we can manage the infrastructure of network and many different system components.
- Using SSH we can transfer files by using SSH file transfer (S FTP) or Secure Copy Protocol (S C P).
- It is used in Cloud Computing for providing security.
Conclusion!
Gaining an in-depth understanding of the underlying how SSH works can help users understand the security aspects of this technology. Most people consider this process to be extremely complex and un-understandable, but it is much simpler than most people think.
If you’re wondering how long it takes for a computer to calculate a hash and authenticate a user, well, it happens in less than a second. In fact, the maximum amount of time is spent on transferring data across the Internet.
